Frustrated with your carefully crafted email campaigns landing in the dreaded spam folders? You’re not alone. Today’s inboxes are bombarded with messages, making it tough for legitimate emails like yours to reach their intended recipients.
But fear not! By understanding and implementing email authentication, you can significantly improve your email deliverability and ensure your important messages find their way to the inboxes they belong in. To fix this, you need to understand a few technical things.
SPF and DKIM are important email authentication protocols that help keep your emails secure. SPF confirms that emails are really from your domain, while DKIM checks if they’re genuine from authorized servers.
This boosts email security against spam, phishing, and spoofing. Don’t worry we’re here to help explain all this in simple terms, even if you’re not a tech expert.
What is email authentication?
The FBI Internet Crime Complaint Center (IC3) recently released an updated Public Service Announcement, identifying nearly $51 billion in exposed losses due to business email compromise, or BEC.
To prevent any kind of scam email authentication is essential.
Email authentication is a process used to verify the identity of the sender and ensure the integrity of an email message.
It works by employing various authentication methods to confirm that an email originates from the claimed sender and hasn’t been tampered with during transit.
Let’s say you want to send a letter to your friend, but you’re worried it might get changed on the way. So, before sending it, you get a special stamp with your name on it.
When your friend gets the letter, they check the stamp to make sure it’s really from you. If it matches, they know the letter is real and hasn’t been changed.
In emails, this stamp is called email authentication. It’s a special code added to each email by the sender’s email service.
When it gets to your email service, it checks the code to make sure the email is real and hasn’t been changed. If everything’s okay, the email goes to your inbox. This helps stop fake emails and makes sure only real ones get through.
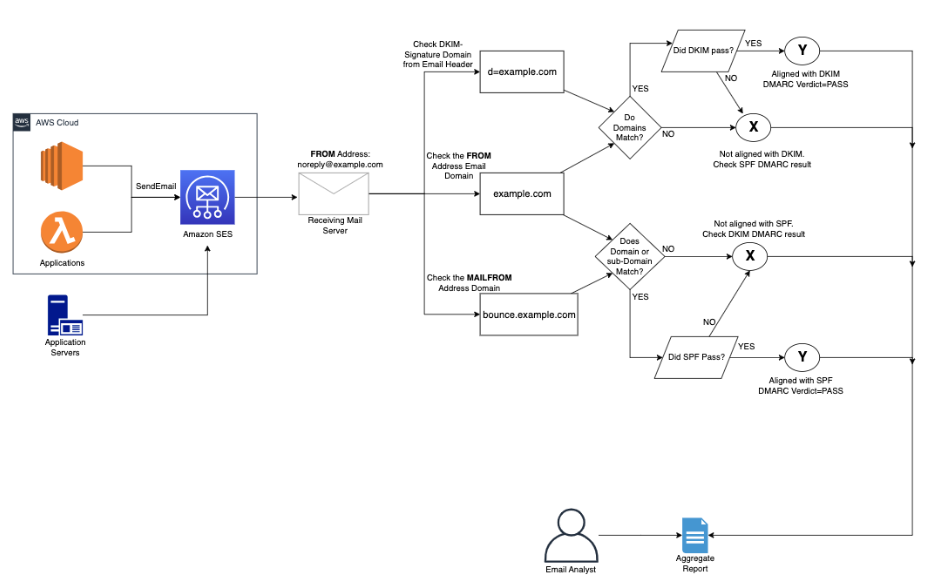
Source: Amazon SES
What is SPF? How does SPF work?
In simple terms, Sender Policy Framework (SPF) is a security measure designed to prevent unauthorized parties from sending emails on your behalf.
Essentially, SPF acts as a communication tool between DNS servers, specifying which servers are allowed to send emails for a particular domain.
This prevents scammers from impersonating you and sending fraudulent emails. With SPF, you can ensure that emails originating from your domain are only sent from authorized mail servers and IP addresses.
It’s crucial to set up SPF records for your domain to protect against email spoofing.
Remember, each domain can have only one SPF record, but within that record, you can list multiple authorized servers and IP addresses.
Why is SPF important for email deliverability?
SPF (Sender Policy Framework) is important for email deliverability because it helps prevent your emails from being marked as spam or rejected by recipient servers.
Here’s why:
- Verification of Sender’s Identity: SPF allows email servers to check if an email is coming from an authorized server associated with your domain. This helps verify the sender’s identity and ensures that the email is legitimate.
- Reduction of Spam and Phishing: By authenticating the sender’s identity, SPF helps reduce the risk of spam and phishing emails. It allows email servers to distinguish between genuine emails from your domain and fraudulent ones from unauthorized sources.
- Enhanced Trust and Reputation: When your emails pass SPF checks, it enhances your domain’s reputation as a sender. This improves the likelihood of your emails reaching recipients’ inboxes instead of being filtered as spam.
Sender Policy Framework (SPF) is a vital email validation standard used to authenticate emails and prevent email spoofing. Misconfigured SPF records can cause validation errors, potentially leading to emails being marked as spam. Read this article to identify common causes of SPF validation failures and provide effective troubleshooting solutions.
How do I authenticate an email with SPF?
To authenticate emails with SPF, you add an SPF record to your DNS server. This record lists the IP addresses authorized to send emails to your domain.
To prevent SPF authentication issues, you must know all IP addresses sending emails from your domain and include them in your SPF record.
To know more about SPF unverified status troubleshooting, read the article
If you use multiple email domains, you’ll need separate SPF records for each to ensure reliable email delivery. Otherwise, the success of sending emails may vary depending on the domain used.
1. Understand your provider
Different email providers have different processes for setting up SPF. First, identify which provider you use (e.g., Gmail, Yahoo, your own custom domain with a hosting provider).
2. Locate your DNS settings
Access your domain’s DNS settings through your provider’s control panel. This is where you’ll modify DNS records, including SPF records.
3. Create an SPF record
Each SPF record specifies authorized IP addresses for sending emails on your behalf. You’ll need to consult your provider’s documentation for specific instructions on creating the record, as the format might vary.
To add an SPF record, edit your domain’s DNS zone file. Include the following line in the SPF record .txt file:
v=spf1 ip4:[IP ADDRESS] -all
Replace [IP ADDRESS] with your email server’s IP address. The “-all” at the end of the record indicates that any other IP addresses should be considered invalid.
Here’s an example of how it might look in a web hosting service. The process may vary slightly depending on the service provider:
v=spf1 ip4:21.43.65.87 ip4:23.45.67.89
include:thirdparty.example.com -all
v=spf1 ip4:21.43.65.87 ip4:23.45.67.89
If you have additional IP addresses, add them by putting a space after the final digit of the preceding IP address and writing “ip4:[IP ADDRESS]” for each additional IP. You can also include third-party domains using “include:[THIRD PARTY DOMAIN]”.
Once you’ve finished, save the SPF record and restart your DNS server. Your emails should now be authenticated with SPF.
4. Publish the record
Once you’ve created the record, save it and publish it in your DNS settings. This process can take up to 48 hours to fully propagate across the internet.
5. Verify your setup
Use online tools like MXToolbox or Sender Policy Framework to verify if your SPF record is correctly published and configured.
Check out this blog to learn more about email domain verification using SPF. Additionally, take a look at how to accomplish this in Desk365.
What is DKIM and how does it work?
DKIM stands for DomainKeys Identified Mail, and it’s like a digital fingerprint for your emails. It helps ensure that the messages you send haven’t been altered in transit, protecting you and your recipients from phishing and other scams.
The DKIM signing process involves three key steps. Firstly, the sender selects the fields to be encompassed within the DKIM record signature, such as the “from” address, the body, and the subject. These chosen fields must remain unaltered during transit to ensure successful DKIM authentication.
Secondly, the sender’s email platform generates a hash of the designated text fields included in the DKIM signature. For instance, the fields:
From: John Smith <john.smith@example.com>
Subject: Important Announcement
Upon hashing these fields, a distinct hash string is generated, which might look like this:
7c64e8d5a8901c49efb3d61e74bc8e2f
This hash string serves as a unique representation of the text fields and is utilized in the DKIM signature process to ensure the integrity of the email content during transmission.
How to set up DKIM record on your server step by step?
DKIM signatures serve as an optional feature in email authentication. Opting to utilize DKIM signatures can enhance the deliverability of emails, particularly with DKIM-compliant email providers.
Different servers may have various methods for implementing DKIM. Let’s now delve into how we can set up DKIM specifically in Amazon SES.
Amazon SES offers three methods for implementing DKIM signatures:
- Easy DKIM: SES automatically generates a public-private key pair and applies a DKIM signature to each message sent from the specified identity.
- BYODKIM (Bring Your Own DKIM): This option allows you to furnish your own public-private key pair, which SES then utilizes to add DKIM signatures to outgoing messages.
- Manual DKIM Signature Addition: For greater control, you can manually incorporate DKIM signatures into emails using the SendRawEmail API.
Let’s see how to set up DKIM record using Easy DKIM,
Configuring an Easy DKIM domain identity involves setting up DKIM-based verification, where you can choose either the default setting of 2048 bits provided by Amazon SES or override it with a selection of 1024 bits. For more information on DKIM signing key lengths and how to modify them, please see the section on DKIM signing key length.
To configure Easy DKIM for a domain:
- Sign in to the AWS Management Console and navigate to the Amazon SES console at https://console.aws.amazon.com/ses/.
- In the navigation pane, under Configuration, select Verified identities.
- Choose the identity from the list where the Identity type is Domain.
Note: If you need to create or verify a domain, refer to the section on Creating a domain identity.
- Under the Authentication tab, in the DomainKeys Identified Mail (DKIM) section, click Edit.
- In the Advanced DKIM settings section, click the Easy DKIM button in the Identity type field.
- Choose either RSA_2048_BIT or RSA_1024_BIT in the DKIM signing key length field.
- Check the Enabled box in the DKIM signatures field.
- Click Save changes.
After configuring your domain identity with Easy DKIM, you must complete the verification process with your DNS provider. Proceed to Verifying a DKIM domain identity with your DNS provider and follow the DNS authentication procedures for Easy DKIM.
Here’s how to set DKIM in some of the other domain hosts:
For further insights into resolving the DKIM unverified status, check out our blog post, Troubleshoot the DKIM Unverified Status.
What is DMARC and how does it work?
In simple terms, DMARC is an email security measure that safeguards your domain from misuse by unauthorized users and enhances your control over email deliverability. It builds upon the SPF and DKIM mechanisms to provide comprehensive protection.
DMARC, short for Domain-based Message Authentication, Reporting, and Conformance, essentially verifies if an email sender is genuine. If an email fails the DMARC check, it’s handled according to the receiver’s DMARC policy, which determines whether to accept, flag, or reject it.
Moreover, DMARC enables receivers to send reports to senders detailing how emails were managed, whether they landed in the inbox, spam folder, or were rejected. This reporting feature ensures transparency in email handling.
A DMARC record is like a set of instructions stored in your domain’s DNS settings. It tells email receivers what to do if an incoming email fails authentication. This record includes a URL where the receiver can send reports about suspicious emails and a policy dictating how to handle them. There are three possible actions:
- None: Only report the issue but don’t take any action.
- Quarantine: Report the problem and move the email to the recipient’s junk or spam folder.
- Reject: Report the issue and bounce the email back to the sender.
While DMARC is not mandatory, most major email providers now follow it as a standard practice to enhance email security. By adjusting DMARC policy options, businesses can strengthen their email defense mechanisms.
DKIM vs SPF?
DKIM and SPF are integral components of email security, working collaboratively within DMARC (Domain-based Message Authentication Reporting and Conformance) to bolster defenses against various threats. While both serve to fortify email integrity and thwart malicious activities, they fulfill distinct roles.
DKIM ensuring message integrity – DKIM verifies the integrity of email content, safeguarding against unauthorized alterations by third parties during transmission. By digitally signing emails with cryptographic keys, DKIM provides assurance that the message remains unaltered from its origin.
SPF prevent domain spoofing – SPF, on the other hand, focuses on preventing domain spoofing by specifying authorized email servers permitted to send messages on behalf of a domain. Through TXT records in the DNS, SPF empowers recipient servers to identify, and block spoofed messages bearing the sender’s domain.
Complementary Protection – While SPF mitigates the risk of unauthorized senders spoofing the domain, it does not address potential message tampering. Here, DKIM steps in to validate the sender’s legitimacy and ensure message integrity throughout transmission.
Integration with DMARC – DKIM and SPF are key components within DMARC, which orchestrates email authentication and establishes policies for handling messages that fail validation. DMARC rules can range from quarantining suspicious emails for manual review to automatically discarding those that fail DKIM and SPF checks.
Think of SPF, DKIM, and DMARC as a security team
- SPF acts as the gatekeeper, checking senders’ authorization.
- DKIM acts as the verifier, ensuring message integrity.
- DMARC acts as the leader, dictating what happens when things go wrong and providing key intelligence for improvement.
A blend of SPF, DKIM, and DMARC is considered the ultimate trio for email authentication. While SPF and DKIM are commonly used, DMARC is gaining traction as an additional layer of protection against spoofing and phishing attacks.